Avoid Being Discovered! How to Prevent Data Forensics from Accessing Your Hard Drives
The arrest of twenty-five Anons in Europe and South America, along with rumors of an FBI sweep on the east coast of the United States, make the situation for hackers precarious. I've been asked a number of concerns in the last few days concerning the removal of private information from hard drives. Concepts appear to cover a wide spectrum, from microwaves to magnets and all in between. I'll now go over some basic information on data forensics, including its operation and precautions you can take.
Anon frequently removes files from his computer, but it only tells half the story—the deleted files are still present. And when his door is kicked in and the FBI grabs his hard drive, they will have access to everything if the negligent anon doesn't take action to remedy that. Be not so anonymous.
Computer Forensics: What Is It? The Individuals on CSI?
The gathering, preserving, analyzing, and presenting of evidence pertaining to computers is known as computer forensics. In conclusion, it aids in identifying the who, what, where, and when of an offense or crime involving computers. Once the federal agents have apprehended you and placed your possessions in evidence crates, they will transport them to the FBI data lab located in Washington, D.C.
An examiner will also attempt to access every file on the subject's computer. This includes currently open files that are encrypted, password-protected, hidden, erased, and invisible. A computer forensics investigation frequently gathers data that is not generally accessible or readable by the normal user of the system, such as bits and pieces of information placed in the "slack space" between files that are already in existence. It takes specialized knowledge and equipment to get this kind of data or proof.
How to Keep Yourself Safe
Data-wiping overwrites all data space on a storage device, replacing valuable data with junk data, whereas file erasure only designates file space as ready for reuse. The overwritten data may consist of random patterns or zeros (a.k.a. "zero-fill"), depending on the technique employed. For this reason, wiping data alone is never sufficient. To make sure your removal is finished, you need to be proactive.
To do this, we're going to use an excellent boot disk known as DBAN.
Step 1 Obtain and Burn DBAN
The 2.2.6 Beta version is available for download on Sourceforge. Burning the.ISO on a blank CD or DVD is the only thing left to do after you have it. After inserting the media into your disk, turn on your computer again. Most computers are configured so that the CD drive attempts to boot up before the hard drive. In the event that the CD drive is not being booted by your computer, you will need to access your BIOS setup and adjust the boot priority order.
Step 2 Boot and Run!
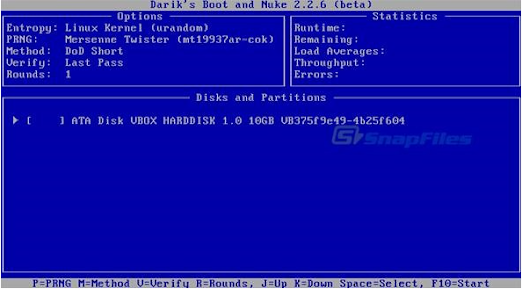
When the CD plays, the screen that appears is as follows:
To launch DBAN in interactive mode, we just need to hit the Enter key here. Your hard drive should be cleaned from the primary menu that is displayed below.
The following screen informs us that DBAN is prepared to begin working; the DoD Short wipe approach is the default and should be sufficient for our needs.
It will begin when you hit the space bar to select. However, be advised that it takes some time to complete the DoD wipe, particularly on bigger hard drives. but not for as long as a term in a prison.
To sum up, DBAM is an excellent tool for hard drive cleaning. When I travel, I keep a duplicate of it in my laptop bag, and you need to too. It functions better than the majority of other tools I have used and is quick and simple. Take caution because, very obviously, zapping the incorrect hard disk will not allow for recovery!



Comments
Post a Comment