Part 3: Digital Forensics for the Aspiring Hacker: Recovering Deleted Files
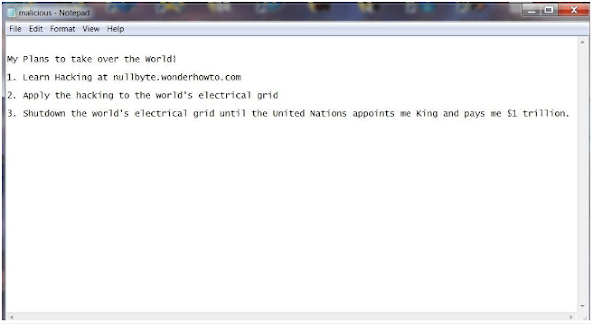
My tenderfoot hackers, welcome back! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them. Windows File System's As the majority of the victims' systems are probably Windows-based, let's concentrate on Windows systems and their file systems. Older Windows systems may still use the FAT filesystem, while the majority of modern Windows systems use the NTFS filesystem. Actually, if you are using a flash thumb drive, it is most likely formatted using the outdated FAT file system, which enables you to use it with ANY operating system, including Mac OS X and Linux. NTFS The "new" Windows, Windows NT (thus, NT File System), was being devel...

